A ransomware attack uses malware to encrypt systems and data, for the purpose of demanding ransom for decrypting the files. In a ransomware attack, cybercriminals hold your data and systems hostage. If you don’t have data protection strategies in place, a ransomware attack can result in a catastrophic data breach and disrupt business continuity. Read on to learn how to create a ransomware data recovery strategy, including five methods for recovering ransomware encrypted files.
This is part of an extensive series of guides about network security.
In this article, you will learn:
Related Article: List of Ransomware Attacks
What Is a Ransomware Attack?
A ransomware attack is an attack carried out with malware that encrypts your systems and data. Attackers demand a ransom to decrypt your data, allowing you to access it again. Often, attackers ask for payment in cryptocurrency since it is anonymous and less traceable. The ransoms demanded can be minor or can be for large sums of money.

DOWNLOAD THE RANSOMWARE PROTECTION BUYER’S GUIDE
How to Prevent Ransomware: Building Your Ransomware Data Recovery Strategy
The most effective way to protect your systems against ransomware is to prevent it from being installed. The next best way is to anticipate how it can enter your systems and what data is likely to be targeted. This helps you focus protections and ensure that data is backed up before an attack.
To develop a robust data protection strategy, it’s often easiest to start with your data and work from there. The following steps can help you develop a solid ransomware data recovery strategy.
-
- Inventory your data—create an inventory of your data to determine how data should be categorized and where it is stored. Categories might include critical, valuable, regulated, or proprietary. Once you have an inventory, you can determine how data needs to be protected and you can initiate data backup.
- Identify your endpoints—you need to know where your endpoints are to identify where ransomware infections might come from. Like with your data, you can categorize endpoints to determine priority and ensure high-value endpoints are protected appropriately.
- Determine your recovery plan—create a ransomware data recovery plan for all assets and data, prioritizing mission-critical ones. You should be able to either restore or rebuild all assets, preferably from a master backup or image.
- Protect your backups—backups are only helpful when secure and accessible. You need to make sure your backups are as protected as your systems and data to ensure that you can restore data from backups and that the data you are restoring is reliable.
- Duplicate data offsite—you should store at least one copy of data either offline, offsite, or both. This ensures that even if on-site backups are encrypted with ransomware you still can restore data. When storing these copies, make sure to secure data just as you would for the primary copy.
How to Recover Ransomware Encrypted Files
If you have already been affected by ransomware, there are several methods you can try to restore ransomware encrypted files, rather than paying your attacker.
Restore From Backup
One of the most effective methods to recover your encrypted files is by restoring from a backup. A backup is a copy of your files stored separately from your computer, typically on an external hard drive or in the cloud. Having a reliable backup system in place can save you from the hassle of dealing with ransomware attacks.
Regular backups are essential because they ensure that your data is safe and secure, even in the event of a ransomware attack. By regularly backing up your files, you can quickly restore them if they become encrypted by ransomware. This not only saves you time but also prevents you from having to pay the ransom to regain access to your files.
There are many backup solutions available, ranging from manual backups to automated cloud-based services. When choosing a backup solution, consider factors such as the volume of data you need to back up, how often you want to perform backups, and your budget. It’s crucial to select a backup solution that meets your needs and provides you with peace of mind.
Related Article: Ransomware Backup – How to Get Your Data Back
Windows System Restore
Windows System Restore is a built-in feature that allows you to revert your Windows system’s files, programs, and settings to a previous state. This can be helpful in recovering files encrypted by ransomware, as it may restore your files to a point before the encryption occurred.
Windows System Restore works by creating “restore points,” which are snapshots of your computer’s system files and settings at a specific point in time. These restore points can be created manually or automatically by Windows. If your files are encrypted by ransomware, you may be able to use a restore point created before the encryption to recover your files.
While Windows System Restore can be helpful in recovering encrypted files, it does have some limitations:
- It only restores system files and settings, not personal files, so it may not be able to recover all of your encrypted files.
- If the ransomware has infected your computer’s restore points, you may not be able to use this method to recover your files.
To restore your Windows system to a previous state:
Go to Control Panel and select System and Security. Next, choose Backup and Restore. When you select “Restore files from backup” you are taken to a wizard that helps you complete the process.
Windows File Versions
Another method to recover ransomware encrypted files is by using Windows File Versions. This feature, available in Windows 7, 8, and 10, automatically creates previous versions of your files as you work on them. These previous file versions can be used to recover files encrypted by ransomware.
Windows File Versions works by creating copies of your files each time you save them or at specific intervals set by Windows. These file versions are stored separately from the original files and can be accessed through the File Explorer. If your files are encrypted by ransomware, you can use these previous versions to recover your data.
While Windows File Versions can be a helpful tool in recovering encrypted files, it does have some limitations:
- You must have the feature enabled on your computer for it to work.
- It may not have previous versions of all your files, especially if the feature was enabled after some of your files were already encrypted by ransomware.
To restore previous file versions in Windows:
- Right-click the file you want to restore and select Properties.
- Select the “Previous Versions” tab.
- Select from the list of restore points the version that you want to restore. You can verify the version by selecting View from the options.
- Once you have verified your version, you can either create a copy (using Copy) of the file in the same directory as your encrypted file or you can overwrite the encrypted file (using Restore).
Data Recovery Software
If you are not trying to recover a Windows device or if you just want to use a third-party solution, you can try using data recovery software. This software can be helpful if you do not have backups or recovery points to restore from. If you need to recover ransomware files, you can use dedicated ransomware backup solutions.
You can use data recovery software to:
- Extract corrupted or deleted data from storage devices
- Repair hard drive partitions or de-format drives
These solutions work for both system-created and user-stored data and can recover data from most storage devices. This includes flash drives, hard disks, external storage, and tape drives. This software can also help you recover corrupted or mistakenly deleted data. A few popular solutions are Stellar Recovery, Prosoft Data Rescue, and Disk Drill.
Ransomware Decryption Tools
Ransomware decryption tools are specialized software programs designed to decrypt files encrypted by specific ransomware strains. These tools are typically developed by cybersecurity experts and can be an effective method for recovering encrypted files without paying the ransom.
There are several websites and resources available that provide ransomware decryption tools. It’s important to use a reputable source when downloading decryption tools, as downloading from untrustworthy sources can result in further malware infections. One trusted source is the No More Ransomware project.
Ransomware decryption tools are not available for all ransomware strains, and their effectiveness can vary depending on the specific ransomware variant and encryption method used. Additionally, new ransomware strains are constantly being developed, so a decryption tool may not be available.
To use a ransomware decryption tool:
- Identify the ransomware strain that encrypted your files. This information may be included in the ransom note or can be determined using cybersecurity tools.
- Once you have identified the ransomware strain, search for a decryption tool specifically designed for that strain. Download the tool from a reputable source and follow the provided instructions to decrypt your files.
Ransomware Data Recovery With Cloudian
Cloudian® HyperStore® is a massive-capacity object storage device that can help you store data in a way that is resilient to Ransomware and recover more easily from attacks.
HyperStore can store up to 1.5 Petabytes in a 4U Chassis device, allowing you to store up to 18 Petabytes in a single data center rack. HyperStore comes with fully redundant power and cooling, and performance features including 1.92TB SSD drives for metadata, and 10Gb Ethernet ports for fast data transfer.
Cloudian storage devices can be deployed:
- As a backup target for data protection applications including Rubrik, Commvault, and VERITAS.
- As an enterprise synch-and-share solution allowing client systems to synchronize data and maintain a copy of critical files on a central repository.
- As a file server used by client systems to directly save important files.
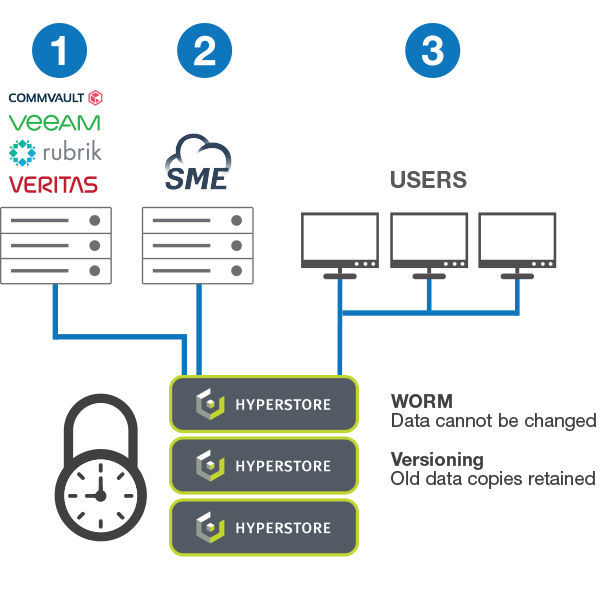
- Write Once Read Many (WORM)—Cloudian ensures that data, once written, cannot be changed or deleted until a specified time has passed. Because the data cannot be modified, it cannot be encrypted rendering ransomware ineffective. WORM is available as a system-level function of Cloudian secure storage devices. Read more about Cloudian’s S3 Object Lock.
- Data Versioning—Cloudian creates a new copy of the data when changes are made, while retaining the original copy for a specified period. If malware encrypts a file, a copy of the unencrypted file still exists.
Learn more about Cloudian’s ransomware backup solutions.
Learn More About Ransomware Data Recovery
Keeping Up with Data Protection Regulations
Data Availability: Ensuring the Continued Functioning of Business Operations
How You Can Maintain Secure Data Storage
Data Encryption: An Introduction
Data Protection in the Cloud: Challenges and Best Practices
See Our Additional Guides on Key Data Breaches Topics:
Data Backup Guide
- Data Archives and Why You Need Them
- Backup Cloud Storage: Ensuring Business Continuity
- Backup Storage: Cloud vs On-Premises
Data Protection Guide
- GDPR Data Protection
- Office 365 Data Protection. It is Essential
- Keeping Up with Data Protection Regulations
Health Data Management Guide





