Ransomware attacks have caused many organizations to lose critical or sensitive data. While preventive measures are the best solution for ransomware, once an attack has already occurred, the best chance to recover the data is to maintain regular data backups. Protecting your data is critical—take measures to prevent backups from getting encrypted by ransomware as well.
This is part of series of articles about ransomware data recovery.
In this article you will learn:
• What is a ransomware attack?
• What is a target for ransomware?
• How to protect backups from ransomware
• Using the 3-2-1 backup strategy
• Ransomware-resilient backup from Cloudian

DOWNLOAD THE RANSOMWARE PROTECTION BUYER’S GUIDE
What is a Ransomware Attack?
Ransomware is a form of malware that prevents users from accessing their files. When ransomware infects a system, it starts searching for valuable files and encrypting them. Files are encrypted using asymmetric key encryption, where attackers hold the private key that can decrypt the files.
Ransomware displays a ransom notice to users, usually by replacing their desktop background or placing a text file with instructions in the file folders it attacked. The ransom notice demands payment, which may be between hundreds and several thousand dollars, to be paid in cryptocurrency to keep the attack anonymous.
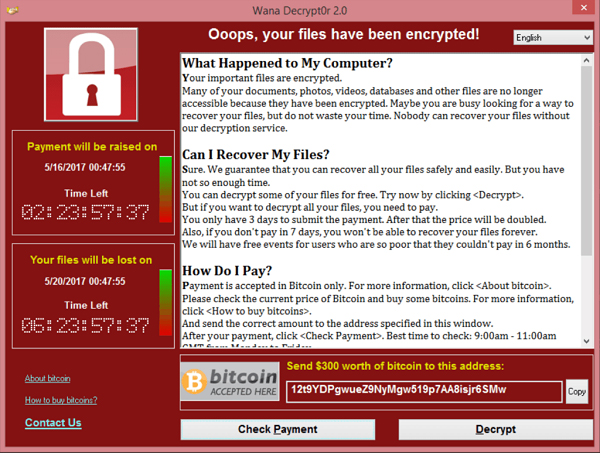
WannaCry ransomware notice
The ransom notice typically specifies a deadline after which the victim’s files will be destroyed. In many cases, even after victims pay the ransom, the attackers fail to release the files.
Common types of Ransomware include WannaCry, Cerber, Cryptolocker, NotPetya, and Ryuk.
Who is a Target for Ransomware?
Ransomware can target almost anyone, from home users to small businesses, large enterprises, government or public agencies, and even politicians or celebrities.
- Academic organizations—these organizations are a prime target for ransomware and other types of cyberattacks. They have smaller IT and security groups than businesses of a similar size, budget constraints, a high rate of community file sharing, and large volumes of sensitive data such as intellectual property, research, and financial data of school, staff, and students.
- Healthcare—hospitals and medical devices often use outdated computing devices and software, which may not be patched or suitably updated, making them relatively easy to breach. Cybercriminals know that if hospital data becomes inaccessible, it can threaten the lives of patients. They attack hospitals with ransomware under the assumption that hospital staff will act immediately to restore the data due to its criticality.
- HR departments—human resources systems have access to personnel and financial records that make them attractive targets for ransomware attacks. Hackers often penetrate HR systems by pretending to be job applicants. HR teams are tricked into opening a job application email and executing an attachment infected by malware.
- Government agencies—attackers target governments for obvious reasons, due to their prominence and the sensitive personal data they hold. They assume government bodies will be quick to pay the ransom because they cannot afford to lose data with public or political significance.
- Mobile Devices—mobile devices contain sensitive personal data, such as personal photos and video, credentials to online services, and commonly financial data and access to mobile payments. Because mobile devices are often backed up automatically to the cloud, attackers prefer to obstruct access to a smartphone and request a ransom for allowing access, rather than just encrypting files.
How To Protect Backups from Ransomware
Data backup is the best way to protect yourself against Ransomware. If you have a clean backup of your data when ransomware strikes, and are able to prevent ransomware from reaching the backup and encrypting it too, you have a safe and easy way to recover without paying the ransom.
Follow these best practices to protect your backups against ransomware:
- Maintain an offline backup—keep a secondary offline backup copy. When ransomware strikes, the malware can attack anything that the infected system has access to. Your end-users are unlikely to be backup administrators, but there are indirect paths through which backups can become infected. If this happens, there is no way to recover because both the main copy of the data and the backup will be encrypted. Keeping an offline backup can mitigate this risk. A simple way to do it is to use traditional backup tapes, which are impossible for Ransomware to penetrate.
- Use immutable storage—also known as WORM (Write-Once-Read-Many), immutable object storage can store data in a bucket and lock it to prevent further modification. Most disk-based backup systems protect data at the block level and use changed block monitoring to safeguard files as they are modified; the problem is that ransomware changes many storage blocks, so your back system may end up backing up the now-encrypted files. Immutable storage ensures backups remain unchanged.
- Endpoint protection on backup servers—modern endpoint protection platforms are able to detect ransomware processes as they begin infecting a system, by recognizing their abnormal behavior, even if the type of ransomware is new and unknown to security researchers. They can immediately lock down the infected systems and isolate them from the network to prevent ransomware from spreading. This is extremely useful for all organizational endpoints but is especially important on the backup server itself.
- Increase backup frequency—see how often you are backing up your own data, which determines your recovery point objective (RPO). Backup frequency will determine how much data can be lost in a ransomware assault. Even if you are backing up once a day or once every few hours, consider the cost of losing all the data since the previous backup. Consider backing up mission-critical data at least once per hour.
Using the 3-2-1 Backup Strategy to Mitigate Ransomware Risk
The 3-2-1 rule is a general best practice for recovery and backup, which can also help mitigate ransomware risks. No backup strategy is foolproof, but following the 3-2-1 rule is probably the most powerful approach to prevent data loss.
Here is how 3-2-1 backup works:
- Have at least 3 copies of your information—one main copy and two backups.
- Use 2 distinct media formats—for example, SSD drive and cloud storage.
- Keep 1 of those copies offsite—the most secure option is to store data to a tape and deposit it in a very secure location. Another option is to automatically snapshot data to a disaster recovery location.
Learn more in our detailed guide to S3 object lock and view recent attacks on our ransomware list page.
Ransomware-Resilient Backup from Cloudian
Cloudian® HyperStore® is a massive-capacity object storage device that can store up to 1.5 Petabytes in a 4U Chassis device, allowing you to store up to 18 Petabytes in a single data center rack. HyperStore comes with fully redundant power and cooling, and performance features including 1.92TB SSD drives for metadata, and 10Gb Ethernet ports for fast data transfer.
Cloudian storage devices can be deployed:
- As a backup target for data protection applications including Rubrik, Commvault, and VERITAS.
- As an enterprise sync-and-share solution allowing client systems to synchronize data and maintain a copy of critical files on a central repository.
- As a file server used by client systems to directly save important files.
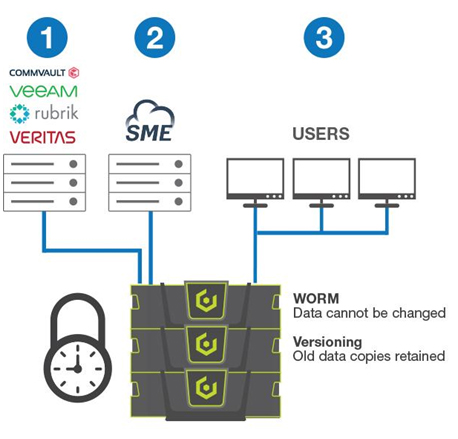
Cloudian protects your data from Ransomware in two ways:
- Write Once Read Many (WORM) – Cloudian ensures that data, once written, cannot be changed or deleted until a specified time has passed. Because the data cannot be modified, it cannot be encrypted rendering ransomware ineffective. WORM is available as a system-level function of Cloudian storage devices. WORM-equipped storage can be deployed in three ways:
- Data Versioning – Cloudian creates a new copy of the data when changes are made while retaining the original copy for a specified period. If malware encrypts a file, a copy of the unencrypted file still exists.
Learn how to lower your storage total cost of ownership with our TCO calculator.


