Cloudian Ransomware Protection Solutions
 When ransomware strikes, hackers encrypt an organization’s data, making that data inaccessible. To obtain the encryption key, the victim pays a ransom, often in a hard-to-trace crypto-currency such as Bitcoin.
When ransomware strikes, hackers encrypt an organization’s data, making that data inaccessible. To obtain the encryption key, the victim pays a ransom, often in a hard-to-trace crypto-currency such as Bitcoin.
Defense Strategies Have Holes
To defend against ransomware, you can either prevent the attack or contain its impact. Attack prevention often involves training programs for users, advising them to avoid “phishing” attacks such as emails whose senders are posing as trusted sources. Another prevention strategy monitors emails and network activity to detect unusual behavior.
Finally, you can simply isolate critical systems behind additional layers of firewalls and password challenges to limit access. In the long run, these preventive solutions ultimately fail as attack technologies evolve.
Object Lock (WORM) Protects Your Data in the Event of Attack
Attacks can strike even the best-prepared, making it essential to mitigate the effects of a successful breach. Here, the best line of defense is at the storage layer, where the data is written.
Learn how Object Lock Protects Your Data
The storage technology to preserve data integrity already exists. Object Lock (also known as WORM, which stands for “write once, read many”) ensures that data, once written, cannot be changed or deleted until a specified time has passed. Because the data cannot be modified, it, therefore, cannot be encrypted, thus rendering the malware ineffective. No one, not even those with admin rights, can change the data, thus also protecting it from employees with malicious intent.
Object Lock (WORM) technology is straightforward to implement: it is available as a system-level function of Cloudian® storage. HyperStore is hardened by the use of HyperStore Shell (HSH) and RootDisable, securing the solution at the system level, even disabling root access to make the solution impregnable. Similar solutions typically have porous root access leaving system-level breaches possible.
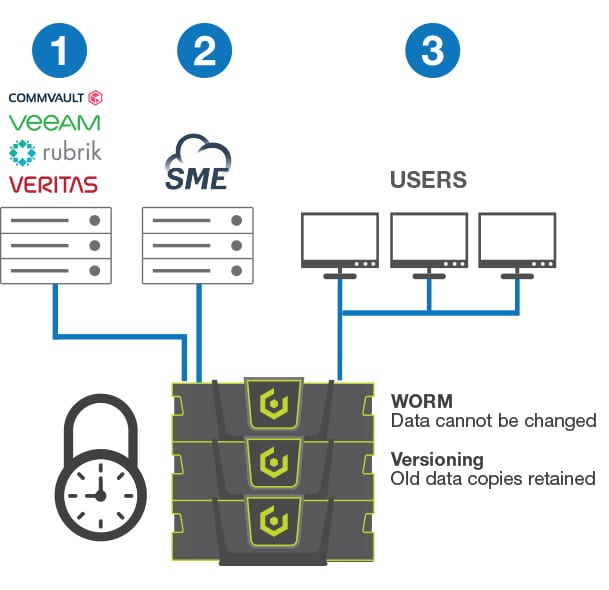
WORM-equipped storage can be deployed in three ways:
1. As a backup target: Cloudian storage can act as a target for popular data protection applications including Veeam, Rubrik, Commvault, and VERITAS. When the Object Lock (WORM) feature is activated on this target, the data written is unchangeable for the specified period. This renders hacks pointless.
2. As part of an Enterprise sync-and-share solution: Client systems are among the most vulnerable to attacks. Loss of data on those devices may severely impact overall productivity, making a protection strategy critical. The Cloudian/SME enterprise file synch-and-share solution works in conjunction with users’ laptops and desktops to maintain a copy of critical files on a central repository where they can be made unchangeable with WORM technology. Data remains on-premises, behind your firewall, immediately accessible when needed.
3. As a file server: A straightforward approach is to directly protect files. When configured with Windows/Linux file services plus WORM functionality, Cloudian systems provide a simple means of protecting files as they are stored.
3 Ways to Protect Data
- Backup target for data protection solution
- Enterprise file synch-and-share
- File storage for Windows/Mac/Linux clients
Data Versioning Offers Flexibility
Another option to address the ransomware challenge is data versioning. This creates a new copy of the data when changes are made, while retaining the original copy for a specified period. Thus, if malware encrypts a file, a copy of the unencrypted file will still exist. The benefit of versioning is flexibility: you can erase the old copies at any time to retrieve capacity or comply with data governance rules.
The benefit of versioning is flexibility: you can erase the old copies at any time to retrieve capacity or comply with data governance rules. Compared with WORM, versioning offers a lower level of protection: In theory, malware could delete the original, unencrypted data. But ransomware typically does not do this. After all, you can’t collect ransom for data that no longer exists.
Both versioning and WORM technologies provide protection where it matters: where the data resides. And they are both easy to integrate and difficult to penetrate.
Ransomware Attacks & Alerts
Comprehensive List of Ransomware Attacks & Alerts through the years
RackTop + Cloudian A Complete Ransomware Solution
 Forrester Report:
Forrester Report:
Four Technologies Combine
to Protect You From
Ransomware Attacks
On-Demand Webinars
- Ransomware Today: What’s New & How to Protect Your Organization with Graham Cluley
- The Rise of Ransomware and How it Has Impacted Enterprise Data Security
- Protecting Your Customers’ Data Against Ransomware with Veeam and HostedBizz
- Outsmarting Ransomware Attackers with Veeam and Cloudian Customer PhoenixNAP
- How to Protect Your Customers’ Data from Ransomware
- Curing the Threat of Ransomware for Healthcare Data with Veeam & Cloudian, with Demo
- Panel Discussion with VMware, Veeam, and Cloudian: The Beginning of the End of Ransomware
- Lock Ransomware Out. Keep Data Safe with Veeam & Cloudian
- Petabytes for Charity: Data Protection for Uncertain Times
- MythBusters Series #2: Are all ransomware protection solutions the same?
- Unlock the Value of your Media Asset Library while Locking out Ransomware




