Most organizations’ cybersecurity defense strategies cover just their network and firewall. But it’s your data that is the hacker’s ultimate prize. Have you focused your defenses mostly on keeping hackers from getting in the door only to leave the very thing he is trying to steal under-protected? Read on for a checklist of security features you should look for to be sure you have a hardened data storage and protection solution.
First, let’s look at some of the latest reasons why this should matter to you, your CISO, and your CIO. October is Cybersecurity Awareness Month and secure data storage has never been more essential – not only to protect against ransomware and other cyber-attacks but also to obtain and keep cybersecurity insurance coverage.
- A well-known hospitality company was threatened with cybersecurity insurance coverage termination due to its lack of having immutable data storage.
- Another company was surprised to discover that its cyber insurance company refused to honor a payout claim because the company’s data storage security lacked policy conformance.
- And a third company, a Cloudian customer, received a 15% discount from its cybersecurity insurance carrier because of its robust data protection.
Cybersecurity insurance provides coverage in the event of malware attacks or data theft. But with the dramatic increase of ransomware attacks, having the right data storage with the right set of security protections can be critical for an organization, including favorably influencing their insurance eligibility, pricing, and even claim conformance. Insurance companies are there to back you up in the event of a breach, but they expect you to do everything in your power to protect against one. It’s literally written in the contract.
Rise of Ransomware Attacks and Costs
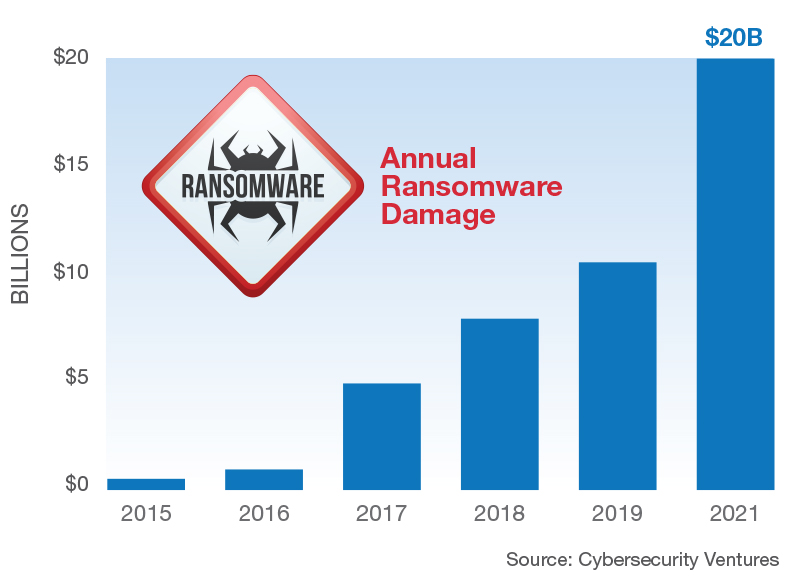
The consequences of ransomware attacks are considerable. This can include downtime, destroyed backups, stolen credentials, and even exposure of stolen data. There is also the lost productivity, the need for crisis management, and reputational harm as well as the restoration and deletion of hostage data and systems. In certain industries, an attack is considered a data breach, a security incident triggering notification requirements.
Also important, costs are rising: the average ransomware payment jumped by 60% to $178,254 between Q1 and Q2 this year according to Coveware, a firm that helps negotiate cyber ransom payments. Ransomware risks are rising as well: an acceleration of ransomware attacks is now forecasted to occur every 11 seconds and global ransomware costs to reach $20 billion in 2021. So, it’s well worth checking to know just how secure your data storage is and whether your protections are up to date.
Data Security Checklist
A fundamental requirement to keeping data secure is immutability which keeps data in a tamper-proof state and enables recovery of an uninfected backup copy in the event of an attack. Immutable data storage is critical for any organization with regulated data and compliance requirements, particularly those industries such as healthcare, education, government, and financial services. System hardening is also important to ensure secure access control. A basic data security and compliance checklist includes:
- Is everything being done to protect your organization’s data?
- Is data storage security considered part of your overall cyber defense strategy?
- Has your organization created a data loss prevention plan?
- Is your data storage immutable and protected against changes, deletions, and made tamper-proof for a specified period of time?
- Does your data security include both data-in-flight and data-at-rest?
- Is your data storage secure from improper access including by internal staff with authorized admin privileges?
- Does your data storage architecture meet regulatory and compliance needs? A technical compliance assessment by Cohasset Associates details how immutable storage addresses these regulatory requirements.
- Have you tested your data backups and archives to make sure they are recoverable?
- Does your organization have cybersecurity insurance, and does it cover data breaches?
- If your organization has commercial insurance instead, does it cover cyber-attacks and data breaches?
Cloudian Data Security
Let’s highlight some of the ways Cloudian data storage helps protect your data from cyber-attacks while also reducing cybersecurity insurance risk:
1. Cloudian military-grade secure data storage (literally, it’s the object storage within the US Dept of Defense enterprise cloud, milCloud 2.0):
- Keeps your data safe and protected with immutable storage and encryption
- Neutralizes attacks with secure shell and access controls such as IAM and LDAP, eliminating the risk of root access and data loss
- Enhances and complements other cyber-threat security protection
2. Cloudian is a market leader for security-enabled data storage with its unique set of security capabilities that taken together, represent the ‘gold standard’ in data storage protection.
– Multiple government security certifications including:
 Common Criteria EAL2
Common Criteria EAL2- FIPS 140-2 Level 1
- SEC 17a-4(f)
- NIST 800-88
- FINRA Rule 4511c
- CFTC Rule 1.31(c)-(d)
- IDW PS 880 (German), §§ 957ff (Swiss)
– S3 Object Lock feature for WORM security
– Data encryption: data-at-rest and data-in-flight
– System hardening with access level controls such as IAM, AD and LDAP
3. Enhanced security analytics and observability with Cloudian HyperIQ: tracking real-time user level activity, providing actionable insights to ensure IT compliance, security and governance.
4. Data storage and protection use cases:
- Integrated with every major backup provider
- Full S3 Object Lock integration with Veeam and Commvault
- Short-term data backup
- Medium and long-term data archive
- Compliance / regulated data during a specified retention period
- Disaster recovery
Get Started Today
Try Cloudian free: https://cloudian.com/free-trial/
Learn more:

Ransomware Protection Buyers Guide

Tackling Data Security and Compliance
Read more about Cloudian here, or contact us for more information.


