Amit Rawlani
Director Technology Alliances, Product & Solution Marketing, Cloudian Inc.
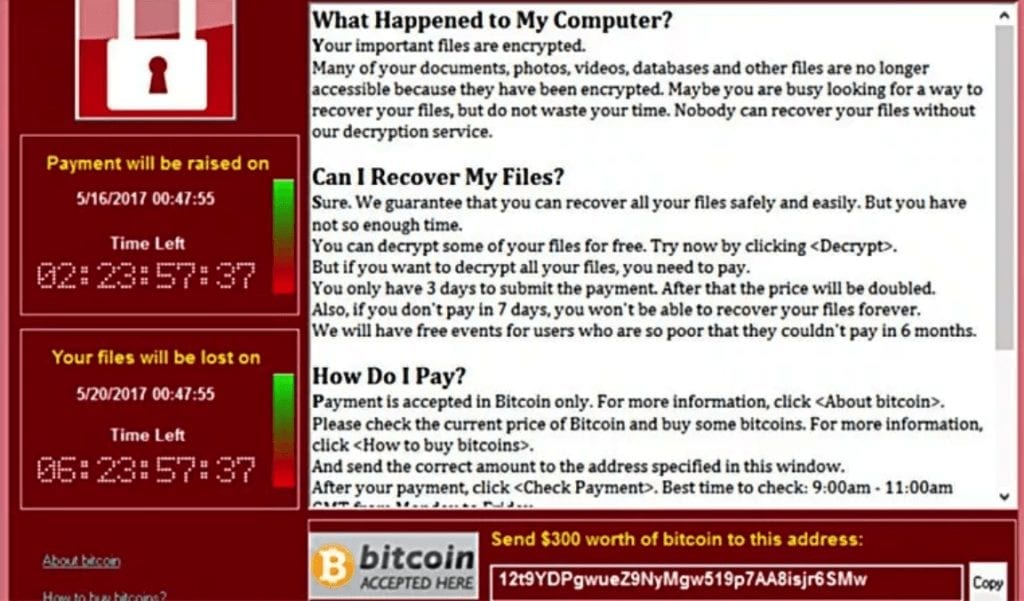
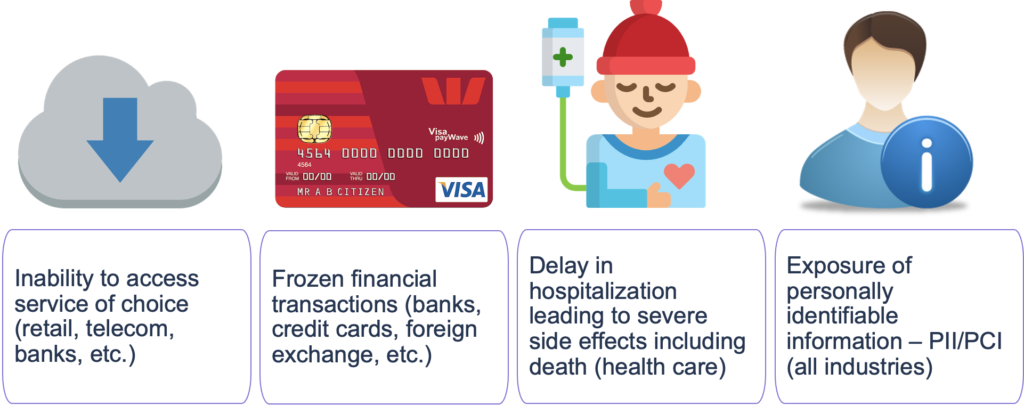
The threat of ransomware should be thought of as serious problem for all enterprises. According to an annual report on global cyber security, there were 304 million ransomware attacks worldwide in 2020 — a 62% increase from 2019. While most IT organizations are aware of the continuously rising threat of ransomware on traditional applications and infrastructure, modern applications running on Kubernetes are also at risk. The rapid rise of critical applications and data moving into Kubernetes clusters has caught the attention of those seeking to exploit what is perceived to be a new and emerging space. This can leave many organizations ill prepared to fight back.
Kubernetes Vulnerabilities
Kubernetes itself and many of the most common applications that run in Kubernetes are open-source products. Open-source means that the underly code that makes up the applications is freely available for any to review and find potential vulnerabilities. While not overly common, open-source products can often lead to exploitable bugs being discovered by malicious actors. In addition, misconfigured access controls can unintentionally lead to unauthorized access to applications or even the entire cluster. Kubernetes is updated quarterly, and some applications as often as every week, so it’s crucial for organizations to stay up to date with patching.
Surprisingly, many organizations that use Kubernetes don’t yet have a backup and recovery solution in place — which is a last line of defense against an attack. As ransomware becomes more sophisticated, clusters and applications are at risk of being destroyed, and without a means to restore them, you could suffer devastating data and application loss in the case of an attack.
What to Look for In a Kubernetes Ransomware Protection Platform
When looking to an effective defense against ransomware in your K8s environment, think about these four core capabilities:
- Backup integrity and immutability: Since backup is your last line of defense, it’s important that your backup solution is reliable, and it’s critical to be confident that your backup target storage locations contain the information you need to recover applications in case of an attack. Having guaranteed immutability of your backup data is a must.
- High-performance recovery: No one wants to pay a ransom because it was faster to unencrypt your data than recover it from your backup system. The ability to work quickly to recover resources is critical, as the cost of ransom typically increases over time. Being confident that your recovery performance can meet target requirements even as the amount of data grows over time.
- Operational Simplicity: Operations teams must work at scale across multiple clusters in hybrid environments that span cloud and on-premises locations. When you’re working in a high-pressure environment following a ransomware attack, simplicity of operations become paramount.
Cloudian and Kasten by Veeam Have the Solution
Kasten By Veeam and Cloudian have teamed to bring a truly cloud native approach to this mission critical problem. The Kasten K10 data management software platform has been purpose-built for Kubernetes. K10’s deep integrations with Kubernetes distributions and cloud storage systems provide for protection and mobility of your entire Kubernetes application. Cloudian’s HyperStore is an enterprise-grade S3-compatible object storage platform running in your data center. Cloudian makes it easy to use private cloud storage to protect your Kubernetes applications with a verified integration with Kasten. With native support of the cloud standard S3 API, including S3 Object Lock data immutability, Kasten and Cloudian offer seamless protection for modern applications at up to 70% less cost than public cloud.
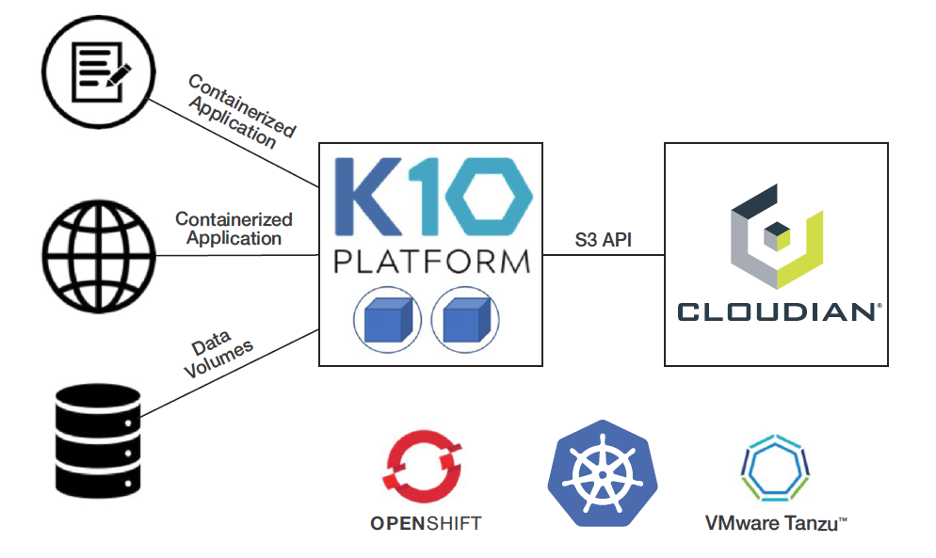
Fast recovery: Cloudian provides a local, disk-based object storage target for backing up modern apps using Kasten K10 over your local, high-speed network. The solution lets you backup and restore large data sets in a fraction of the time required for public cloud storage, leading to enhanced Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO).
Security and Ransomware Protection
Cloudian is a hardened object storage system that includes enhanced security features such as secure shell, encryption, integrated firewall and RBAC/IAM access controls to protect backup copies against malware. es in a shared-storage environment. In addition, to protect data from ransomware attacks, Cloudian HyperStore and Kasten support Object Lock for air-tight data immutability all the way up to the operating system root level.
Kasten-Validated Solution
Cloudian is Kasten-validated to ensure trouble-free integration. Kasten’s native support for the S3 API enables seamless integration with Cloudian HyperStore.
Easy as 1-2-3
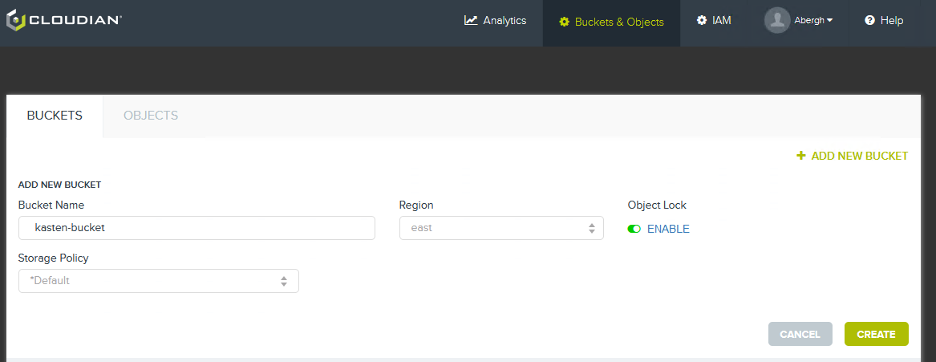
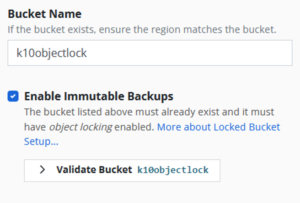
Setting up Kasten K10 and Cloudian Ransomware Protection is as simple as 3 easy steps:
1. Create a new target bucket on Cloudian HyperStore and enable Object Lock.
2. After Kasten K10 installation, check the “Enable Immutable Backups” box when adding a target S3 object storage bucket.
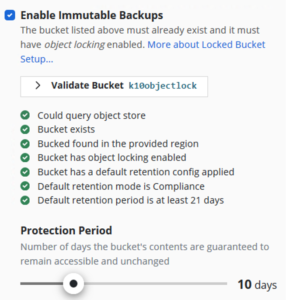
3. Validate the Cloudian object storage bucket and specify your protection period.
GET STARTED WITH KASTEN K10 TODAY!
- Try the full-featured and free Edition of Kasten K10 with a fast and easy install.
- Watch and read customer webinars and case studies.
- Kasten K10 Data Sheet
- Try Cloudian free in your data center for 45 days
- Cloudian + Kasten By Veeam for Ransomware Protection



 Adam Bergh
Adam Bergh
 Amit Rawlani, Director of Solutions & Technology Alliances, Cloudian
Amit Rawlani, Director of Solutions & Technology Alliances, Cloudian Let’s take a look at the importance of back-up protection in the era of ransomware.
Let’s take a look at the importance of back-up protection in the era of ransomware.