In today’s data-driven world, securing sensitive information is of utmost importance for organizations seeking solutions that offer top-tier security and seamless integration with their existing key management infrastructure. At Cloudian, we recognize the critical need for robust data protection, especially for users in public administration, healthcare, and finance. To meet the diverse needs of our customers, Cloudian has implemented the industry standard KMIP in our HyperStore 7.5.1 software version, thus solidifying its position as a leading and secure object storage solution.
What is KMIP?
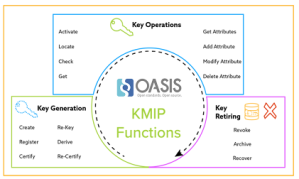 The Key Management Interoperability Protocol (KMIP), developed by the Oasis Key Management Interoperability Protocol Technical Committee, is a widely adopted industry standard for managing cryptographic keys and security objects.
The Key Management Interoperability Protocol (KMIP), developed by the Oasis Key Management Interoperability Protocol Technical Committee, is a widely adopted industry standard for managing cryptographic keys and security objects.
The Significance of KMIP
As Cloudian customers increasingly demand external key management servers for data encryption, KMIP provides a robust solution to ensure compatibility with various Key Management Servers (KMS). It ensures that compliant KMS offerings provide consistent functionality, full key lifecycle support, scalability, and security, to simplify integration into existing security and key management processes. KMIP enables organizations to manage cryptographic keys centrally, ensuring higher security and regulatory compliance.
Benefits of Using KMIP
 Interoperability: KMIP provides a standardized protocol for key management, allowing diverse vendors and systems to communicate effortlessly. Support for KMIP promotes interoperability among key management systems, ensuring compatibility and simplifying integration efforts.
Interoperability: KMIP provides a standardized protocol for key management, allowing diverse vendors and systems to communicate effortlessly. Support for KMIP promotes interoperability among key management systems, ensuring compatibility and simplifying integration efforts.- Centralized Key Management: With KMIP, organizations can centrally store, manage, and access cryptographic keys and related objects. This centralized approach enhances security, simplifies key lifecycle management, and reduces administrative overhead.
- Scalability: KMIP supports scalable key management solutions, allowing organizations to efficiently manage many cryptographic keys across multiple systems and devices. It allows for centralized control and administration, making it easier to control key management operations as the organization grows.
- Enhanced Security: KMIP incorporates robust security measures to protect cryptographic keys and objects. Secure communication channels, authentication mechanisms, and encryption techniques ensure key management operations’ confidentiality, integrity, and availability.
- Vendor Neutrality: KMIP promotes vendor neutrality, allowing organizations to choose key management solutions from different vendors without being locked into a specific proprietary system. This flexibility enables organizations to select the most suitable solution based on their requirements, interoperability needs, and budget, thus promoting competition and innovation.
- Compliance and Auditing: KMIP supports regulatory compliance by providing standardized key management and auditing mechanisms. Organizations can demonstrate adherence to security standards and regulatory requirements by implementing KMIP-compliant key management solutions.
- Future-Proofing: By adopting KMIP, organizations can future-proof their key management infrastructure. As the standard evolves and incorporates new cryptographic algorithms, key types, and security features, KMIP-compliant systems can seamlessly integrate these advancements without major changes.
Supported KMIP Solutions in Cloudian HyperStore
Cloudian has diligently tested and validated the integration with some of the leading KMIP solutions. This provides our customers with a wide range of choices for their key management needs. Solutions tested include:
- Thales CipherTrust Manager: Offers an enterprise-leading key management solution, enabling centralized management of encryption keys and granular access control.
- HashiCorp Vault: Delivers an open-source solution for secure secret and key management, providing encryption mechanisms and integration options with various platforms.
- Fortanix KMS: Provides the unified management of keys, encryption, and secrets across multi-cloud infrastructures with flexible deployment.
Potential Disadvantages of KMIP and How Cloudian Addresses Them
While KMIP offers numerous benefits, it is essential to acknowledge potential challenges when implementing this protocol. Here are the commonly cited challenges and how Cloudian has addressed each:
 Dependency on Vendor Support: Organizations must ensure that their preferred key management vendor fully supports and adheres to the KMIP standard. Cloudian has partnered with Cryptsoft, integrating their well-known KMIP client into the HyperStore to provide interoperability with a wide range of KMS solutions.
Dependency on Vendor Support: Organizations must ensure that their preferred key management vendor fully supports and adheres to the KMIP standard. Cloudian has partnered with Cryptsoft, integrating their well-known KMIP client into the HyperStore to provide interoperability with a wide range of KMS solutions.- Implementation Complexity: Integrating KMIP into a key management system can be complex and resource-intensive. However, Cloudian has integrated native KMIP support within HyperStore, alleviating implementation concerns and making for a seamless process when configuring KMIP based KMS support for Cloudian HyperStore.
- Performance Overhead: KMIP adds communication and processing overhead to key management operations, leading to potential latency and reduced performance compared to proprietary solutions. Cloudian estimates this to be around 15% of processing overhead, which is reasonable for its enhanced security and centralized management.
- Limited Standardization: While widely adopted, KMIP may not cover all key management or cryptographic operations aspects, requiring proprietary extensions or alternative solutions for specific requirements. Cloudian also supports other key management options, such as SSE, SSE-C, and AWS KMS, to cater to specialized needs beyond KMIP’s scope.
- Security Risks: While KMIP aims to enhance security, any standard implementation introduces potential risks. Regular updates and security assessments are necessary to address emerging threats. Cloudian actively monitors and manages security vulnerabilities by promptly patching systems as needed. And, Cloudian’s support for NIST FIPS-validated cryptographic modules ensures the availability of advanced key management features.
- Limited Key Management Features: Organizations with specialized requirements may find the standard’s feature set restrictive in some KMS solutions and may need to explore alternative solutions. The good news is that there are dozens, even likely hundreds of viable choices available.
- Transition Challenges: Migrating to KMIP may involve data migration, system reconfiguration, and potential disruptions to ongoing operations. Cloudian provides guidance and support during the transition process to minimize potential impact.
Conclusion
Incorporating KMIP in the HyperStore 7.5.1 software version is a significant milestone for Cloudian in enhancing data security and ensuring our customers can integrate our object storage solution into their existing key management frameworks. By adopting Cloudian’s HyperStore and combining it with your current key management framework, organizations can achieve and maintain regulatory compliance while safeguarding their most critical asset—their data. Cloudian’s commitment to innovation and security ensures that our customers can rely on us to provide the industry’s leading and most secure object storage solution on the market.
Learn more about Cloudian at cloudian.com.
Or, for a FREE TRIAL, click here.

Glenn Haley, Senior Director of Product Management, Cloudian



