The European Union’s General Data Protection Regulation (GDPR) deadline for implementation has come and gone. Many organizations have achieved a basic level of compliance, so now is the time to dig deeper, tie up loose ends and try to simplify the process. It is also a time for organizations not directly impacted by GDPR to tighten up their data security and protection practices. Organizations around the world need to realize that GDPR was just the initial warning shot and concepts like data privacy are more critical than ever.
**This is a reprint of a blog published by Storage Switzerland on July 24, 2018. Join us for our upcoming live webinar “How to Design a Compliant and GDPR Ready Collaboration System” on July 26th at 11:30 am ET / 8:30 am PT.**
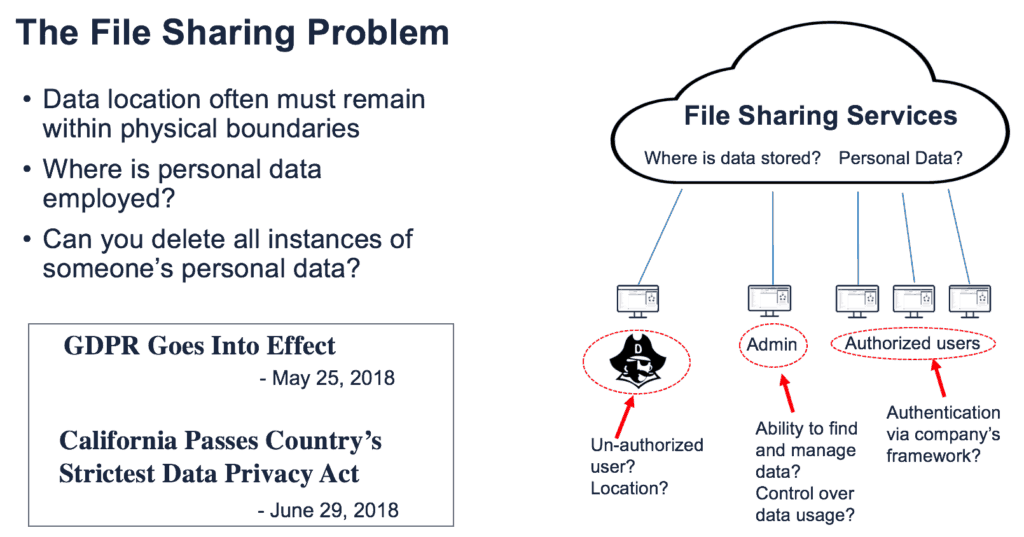
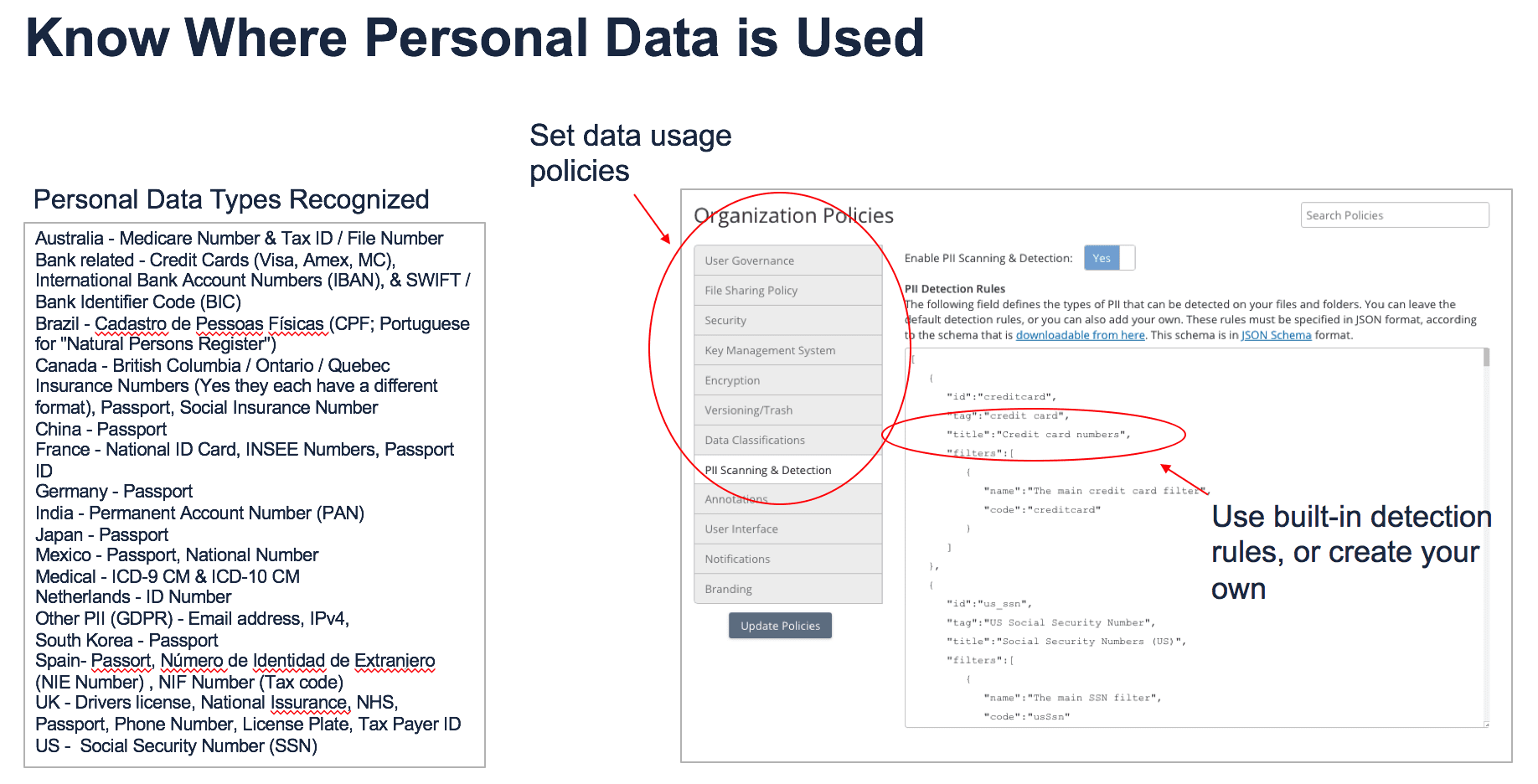
An area to pay attention to is user data. These are files that users within an organization create and share with both internal employees and external business partners. The protection, management, and compliance with user data is one of the more overlooked topics in the organization, but it is also one of the data sets most susceptible to a breach.
A major weakness is how users share their data with external sources. IT, today, has very little control over how users share data and even less oversight as to when they share data. When sharing data, most users today still use consumer-grade cloud-based file sync and share services. These services provide IT with almost no control over with whom and for how long that data is shared.
Enterprise File Sync and Share May Not Be Enough
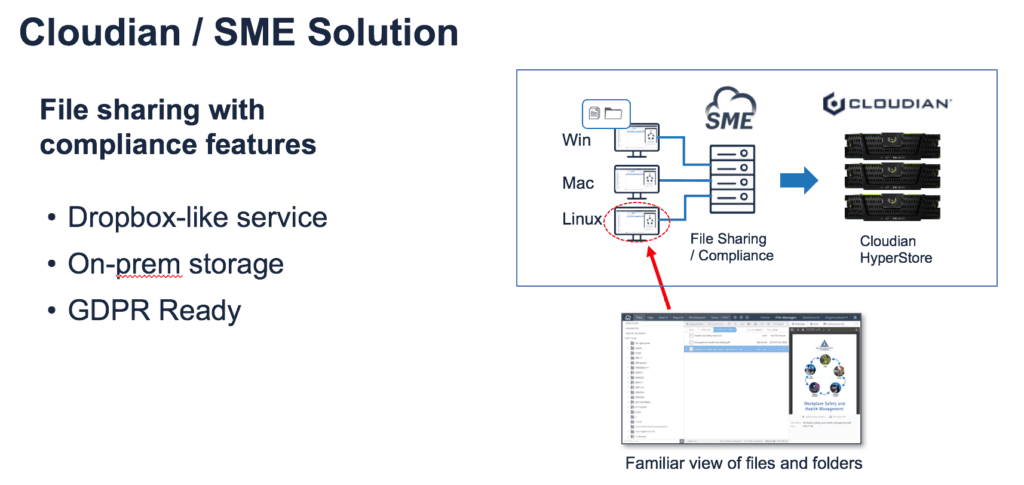
The immediate answer to a file sharing problem is to move the organization to enterprise sync and share (EFSS). These solutions do provide IT with oversight and control over how and who shares files. The problem is that most providers of these solutions did not design them with compliance in mind. They may encrypt data at rest and in-flight, but compliance with GDPR and the more stringent regulations to come requires more than encryption.
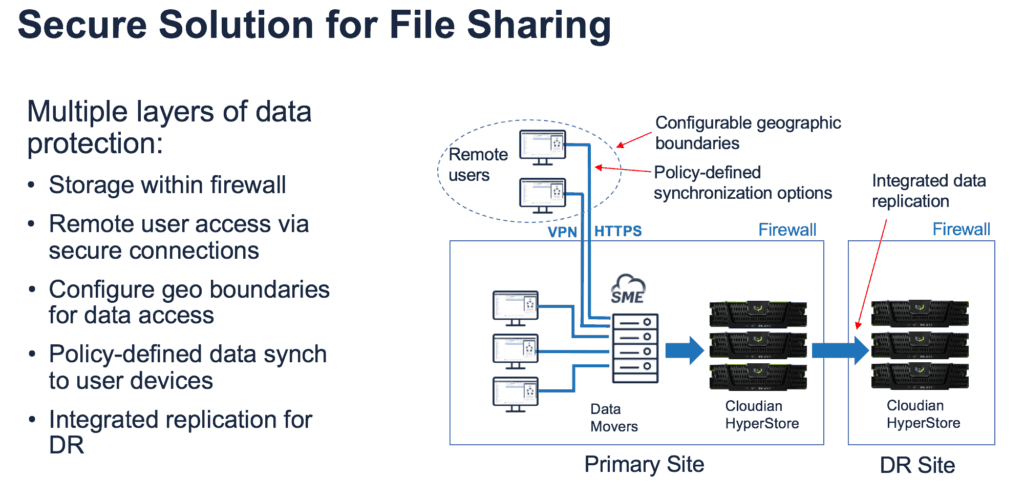
First, a compliant EFSS solution requires identity management. It should integrate with Active Directory, LDP, and SAML for single secure sign-on. Second, the EFSS solution needs to cover more than just one data store. It needs to provide time expiration of shares, password protection, and download restrictions across all corporate data storage. It also needs to provide GEO location restrictions.
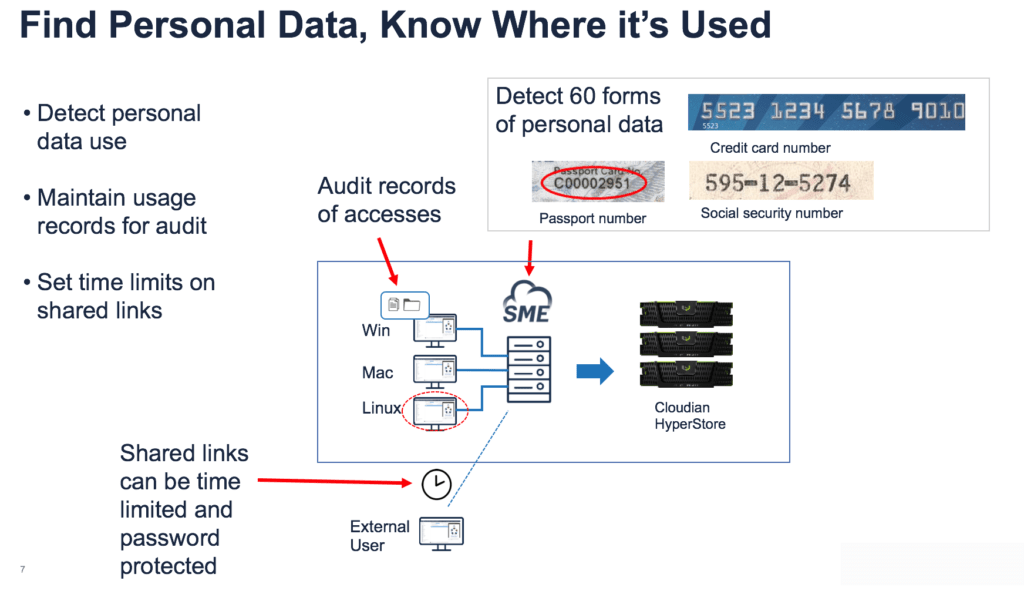
Third, the EFSS solution shouldn’t burden IT. For example, IT can’t be expected to predict every possible reason for sharing or not sharing a file. Instead, the solution should provide sharing policies where users are required to outline why they created a shared link. IT then reviews the sharing justification. Additionally, the solution needs to provide full file event auditing to track file access by date and time as well as by whom and why. File auditing also allows an organization to prove file deletion in response to a right to be forgotten request.
Finally, the EFSS solution needs to provide complete discovery of personal data. Personal data as defined by GDPR is any data that relates to an identified or identifiable natural person. Finding personal data within and across the organization is a big challenge. The EFSS solution needs to index content under its management so authorized users can search it.
StorageSwiss Take
User data is the most exposed data set in an organization, and it is also the most likely to violate regulations and corporate governance policies. Enterprise file sync and share needs to evolve beyond just simple file sharing with encryption to meet the challenge of GDPR and other upcoming data privacy laws. The answer is to manage file data as a unique data set and provide advanced capabilities like auditing and content search.
To learn more about modernizing EFSS as well as how to build a backend storage architecture to support it join us for our upcoming live webinar “How to Design a Compliant and GDPR Ready Collaboration System” on July 26th at 11:30 am ET / 8:30 am PT.